- Intellectual Property Services
- +91-998-809-1807
- info@theipcrew.com
Apple Patent Reveals a Developing Security ID System tied to a National Database to assist Brick and Mortar Merchants & more

Patent Office looks to AI for image searches
October 1, 2020
UK patent applications cannot name AI inventors
October 1, 2020Back in July five patent applications from Apple were published by the US Patent & Trademark Office with the common title “Providing Verified Claims for User Identity (01, 02, 03, 04 and 05). All five patents shared the same patent figures. However, each were distinctly different in covering different aspects of this gigantic project. The differences between the applications were clearly outlined in each of the application’s “Abstract.”
For instance, in Apple’s patent application 20200213294 Apple’s Abstract begins with this line: “A device implementing the subject system may include a processor configured to send, to a service provider, a request for a service provided by the service provider.”
In Apple’s patent application 20200213295 Apple’s Abstract begins with this line: “A device implementing a system for using a verified claim of identity includes at least one processor configured to receive a first request to revoke a verified claim, the verified claim comprising information to identify a user of a device, wherein the verified claim includes a hardware reference key of the device, and wherein the hardware reference key is a public key of a public-private key pair, a corresponding private key of which is securely stored on the device.
Earlier this month a sixth patent application was published by USPTO that is a part of the overall Security ID project, a patent under a different title. Three out of the four inventors in this patent application were not listed on the previous five patents. A fourth inventor was found common on all of the patents in the group. The inventors are listed below:
Mathieu Ciet (Apple France): Cryptography and Security Engineering Manager. Came to Apple from Thales where he as a Public Key Group Manager and Senior Security Engineer.
Michaël Mouchous (Apple France): Software Development Engineers. Came to Apple from Thales where he was a Security Evaluator.
Augustin Farrugia: Senior Director Apple Pay Security, Fraud, iCloud and iTunes. Listed on all six patents relating to this project.
Bruno Benteo: Senior Principle Scientist (left Apple in June 2019)
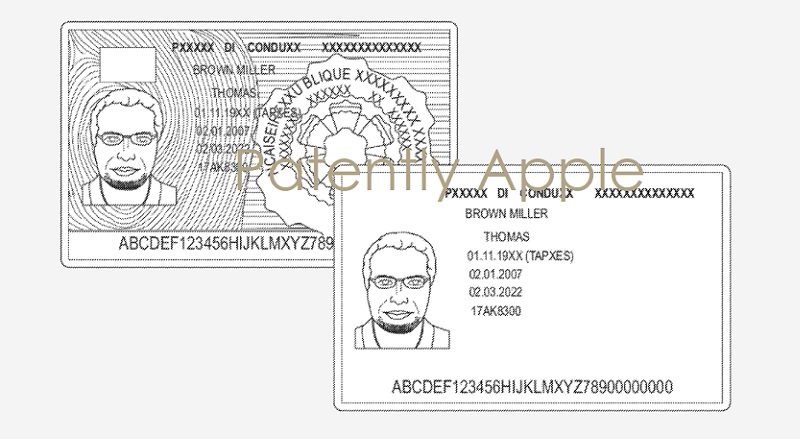
Apple notes in their latest patent application that “in brick and mortar stores, a merchant may have experience in distinguishing an authentic physical ID from one that is not authentic. For example, a physical ID may have multiple security features (e.g., watermarks, textures, engravings, holograms) that are detectable through sight and touch of a person trained on the features.
However, if an image of the ID is provided to an on-line merchant (e.g., which may be an automated service), that service may not be able to detect the security features to verify that the ID is authentic, much less verify if the purchaser is the person to whom the ID was issued.”
The subject system provides for authenticating a user’s physical ID with an identity provider (e.g., an issuer of the ID) to create an electronic ID for a given service or domain of services. During an enrollment phase, the user’s device captures image(s) of the ID (e.g., a driver’s license, passport, or the like) and sends the image(s) to an issuer of the ID (e.g., an agency that issued the ID, such as an agency that issues driver’s licenses), and/or a third party verification service that is capable of verifying the authenticity of the ID. In one or more implementations, the user’s device may capture multiple images of the physical ID, such as an infrared (IR) image and a red-green-blue (RGB) image.
The electronic device may store the electronic ID and use the captured image data to generate a first representation of the ID that is stored on the device. In one or more implementations, the enrollment process may also include locally verifying user-declared (e.g. provided) identity information with identity information printed on the physical ID. In one or more implementations, the first representation may be strongly linked to the user, such as by associating the first representation with biometric information of the user, such as a fingerprint, a set of points corresponding to a scan of the user’s face, and the like.
The first representation may not include the personally identifiable information of the ID. Rather, the first representation may include multiple form factors that are specific to the user’s ID (e.g., the position of a common watermark relative to first/last characters in the user’s name, address, date of birth, and the like). These form factors make it possible for the first representation to uniquely represent the user’s ID without explicitly containing identifying information of the user. Thus, in one or more implementations, the first representation may be stored remotely without exposing any of the user’s personal information.
The subject system provides for authenticating a user’s physical ID with an identity provider (e.g., an issuer of the ID) to create an electronic ID for a given service or domain of services. During an enrollment phase, the user’s device captures image(s) of the ID (e.g., a driver’s license, passport, or the like) and sends the image(s) to an issuer of the ID (e.g., an agency that issued the ID, such as an agency that issues driver’s licenses), and/or a third party verification service that is capable of verifying the authenticity of the ID.
In one or more implementations, the user’s device may capture multiple images of the physical ID, such as an infrared (IR) image and a red-green-blue (RGB) image.
Face ID Plays a Larger Roll in Verifying a user’s ID
In one or more implementations, the user’s device may capture an image of the user and/or a face scan of the user at the time that the physical ID is being enrolled.
The image and/or face scan may be locally used by the user’s device to confirm that the user is the same person pictured in the physical ID.
Since the appearance of the user’s face may change over time, e.g., due to age, the user’s device may periodically obtain images of the user over time (e.g., with the user’s consent, such that the user’s device can compute a link between a current image of the user with the image of the user captured at the time of enrollment). Similarly, the user may allow the device to access prior images of the user, e.g., in a photo library, to a link a current image of the user back to an image of the user that appears on the physical ID (which may have issued several years ago).
Apple’s patent FIG. 3 below illustrates an example process for authenticating an ID, common to all 6 patent applications. It covers the “Enrollment Phase” and the “Sharing Phase.”
New Patent Figures: Apple’s patent FIG. 5 below illustrates an example of different image data that may be used in authenticating an ID; FIG. 6 illustrates an example of security features and user information that may be included on an ID; and finally, FIG. 7 illustrates a flow diagram of an example process for authenticating an ID in accordance with one or more implementations.
Apple’s patent FIG. 7 below illustrates a flow diagram of an example process for authenticating an ID in accordance with one or more implementations.
Apple’s patent application that was published earlier this month by the U.S. Patent Office was filed back February 2020. Considering that this is a patent application, the timing of this next-gen ID security system to market is unknown at this time.
The delay in making this patent application public was simply the sheer depth of reading required to understand the main difference between this latest application versus the other five published earlier this summer. Some Apple patents that are complicated, as this one was, takes time to read, digest and then execute.